Intruder alert


So I’ve been running a Secure shell honeypot for about a year or so, so might as well open up the log files and see what people have been l33ting these days.
For the uninitiated, or for normal people, Secure shell (or SSH) is the traditional method that people log in remotely to Linux (or other unix-based) servers.
A honeypot pretends to be a standard login server, but instead of logging into a real server, it allows would-be hackers to fairly easily guess their way into a sandbox environment, where they can be prodded and observed to see what they get up to.
The honeypot reacts like a normal server would, logging any input that it receives, and pretends to do the sorts of things that people normally try to do when they gain unauthorised access to a computer system (i.e. the electronic equivalent of putting graffiti in the toilet stalls and having their way with the photocopier).
And now, what with Julia Gillard declaring a new War on Technology and throwing money at a new “cyber security centre” (which will certainly be money well spent), it should be every citizen’s prerogative to try to see what the evil commies are getting up to on their computer networks.
So after pretty much a full day of number-crunching and regexing the 2012 logfiles, and a second full day of fiddling about with databases and wordpress, this is what I’ve got:
Executive Summary
| Total number of connections: | 143,039 |
|---|---|
| Total number of unique IP addresses: | 1,488 |
| Total number of logins: | 179,671 |
| (failed): | 175,020 |
| (succeeded): | 4,651 |
| Total number of unique usernames: | 18,413 |
| Total number of unique passwords: | 38,010 |
| Total number of unique username/passwords combinations: | 78,568 |
| Total session time: | 65 days, 7 minutes, 51 hours, 29 seconds |
| (minimum session time): | 0 seconds |
| (average session time): | 39.5 seconds |
| (maximum session time): | 2 days, 13 minutes, 35 hours, 27 seconds |
| Total number of interactive commands: | 394 |
| Total number of non-interactive commands: | 59 |
| Total number of file transfers: | 11 |
- I’m getting about 400 connections a day to the honeypot (the honeypot is exposed via a single public IP address)
- There’s a comparatively small number of IP addresses that are connecting
- About 2-3% of the login attempts are successful (I can increase this percentage if I think it’s worthwhile)
- In total, about 2 months of wallclock time has spent by people logged in to the honeypot
- Only a dozen or so logins have attempted to download a file to the honeypot (presumably with the intention of doing nasty things to the system)
Also note that everything in the reports above and below consist of unauthorised login attempts; there’s no reason why an authorised person would attempt to log into the public-facing side of the honeypot..
Network intrustion statistics
[rn-tabs id=”t1″ selected=”2″]
[rn-tab id=”1″ label=”Daily”]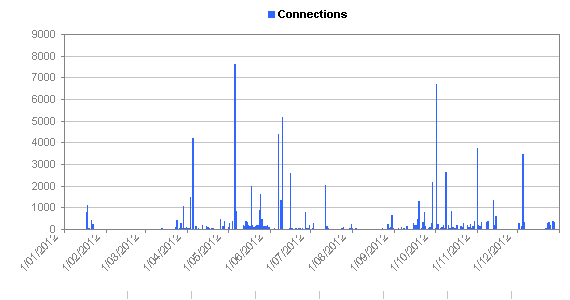 [/rn-tab]
[/rn-tab]
[rn-tab id=”2″ label=”Weekly”]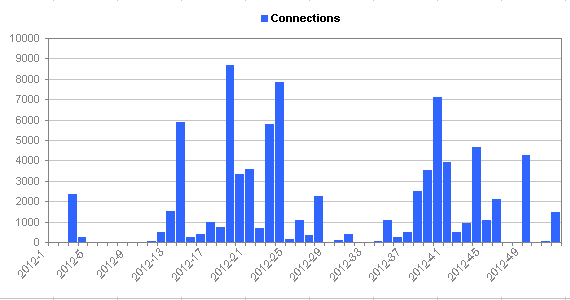 [/rn-tab]
[/rn-tab]
[rn-tab id=”3″ label=”Monthly”]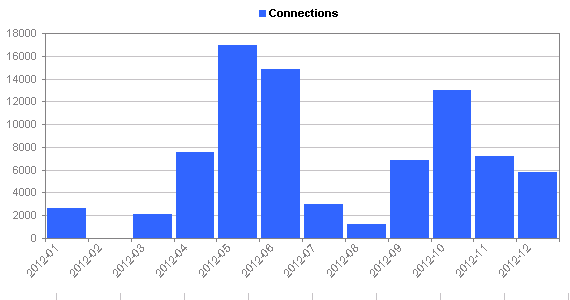 [/rn-tab]
[/rn-tab]
[/rn-tabs]
You can click the tabs above the graph in order to see the same statistics using different histogram intervals.
[rn-tabs id=”t2″ selected=”2″]
[rn-tab id=”1″ label=”Daily”]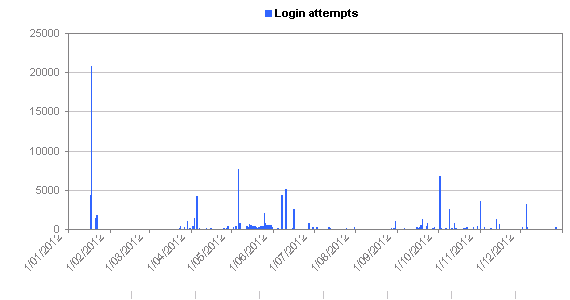 [/rn-tab]
[/rn-tab]
[rn-tab id=”2″ label=”Weekly”]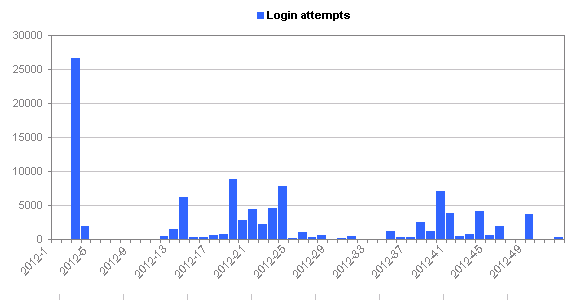 [/rn-tab]
[/rn-tab]
[rn-tab id=”3″ label=”Monthly”]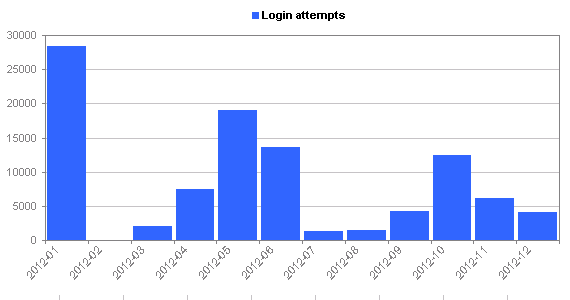 [/rn-tab]
[/rn-tab]
[/rn-tabs]
[rn-tabs id=”t3″ selected=”2″]
[rn-tab id=”1″ label=”Daily”]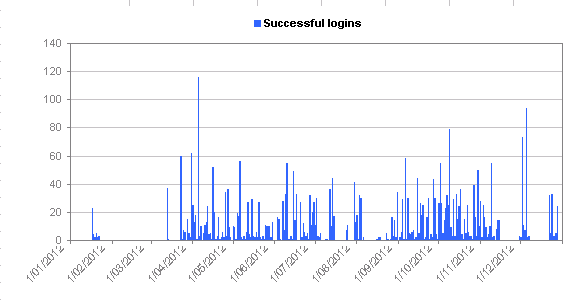 [/rn-tab]
[/rn-tab]
[rn-tab id=”2″ label=”Weekly”]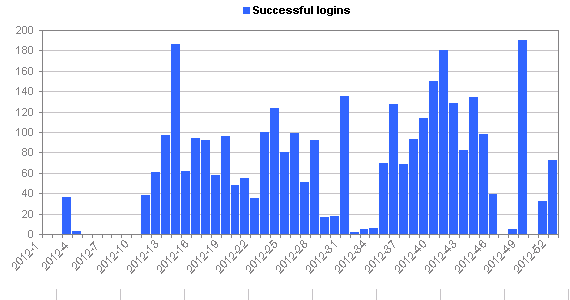 [/rn-tab]
[/rn-tab]
[rn-tab id=”3″ label=”Monthly”]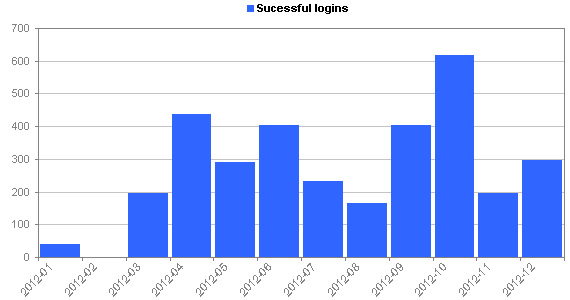 [/rn-tab]
[/rn-tab]
[/rn-tabs]
Long sessions are graphed at 1:00:00
[rn-tabs id=”t4″ selected=”2″]
[rn-tab id=”1″ label=”Daily”]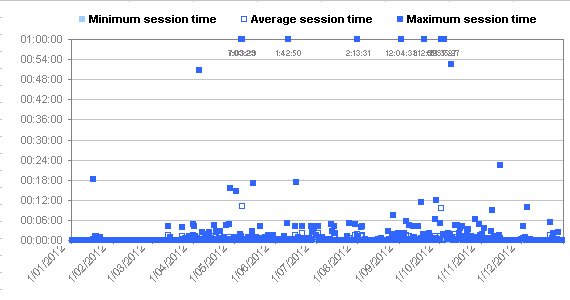 [/rn-tab]
[/rn-tab]
[rn-tab id=”2″ label=”Weekly”]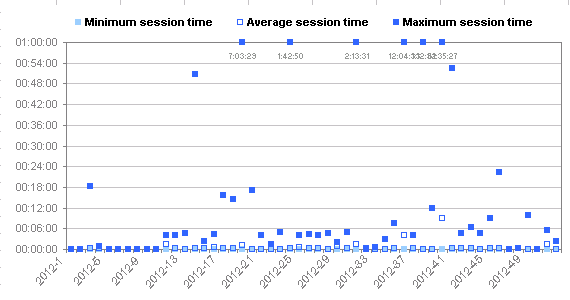 [/rn-tab]
[/rn-tab]
[rn-tab id=”3″ label=”Monthly”]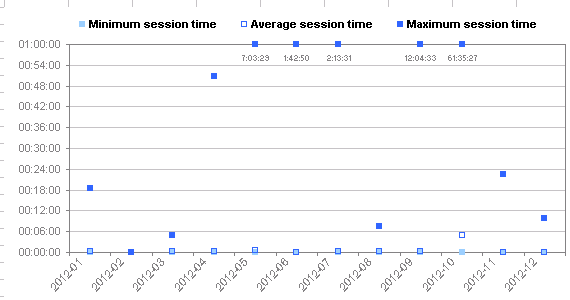 [/rn-tab]
[/rn-tab]
[/rn-tabs]
[rn-tabs id=”t5″ selected=”2″]
[rn-tab id=”1″ label=”Daily”]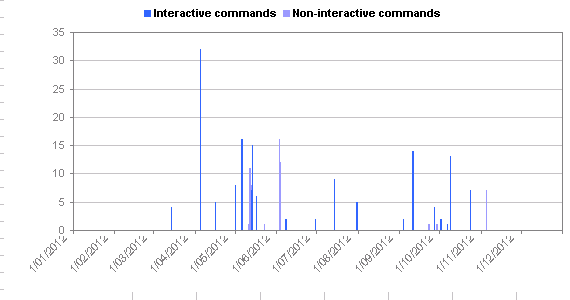 [/rn-tab]
[/rn-tab]
[rn-tab id=”2″ label=”Weekly”]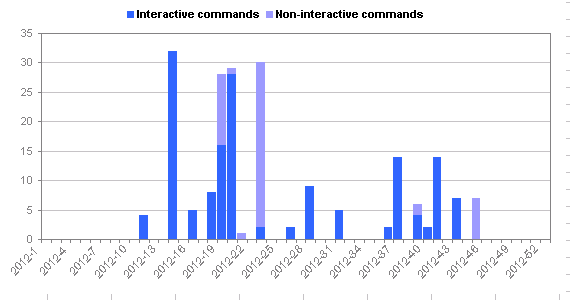 [/rn-tab]
[/rn-tab]
[rn-tab id=”3″ label=”Monthly”]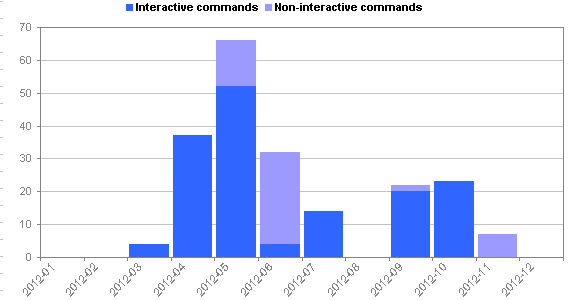 [/rn-tab]
[/rn-tab]
[/rn-tabs]
[rn-tabs id=”t6″ selected=”2″]
[rn-tab id=”1″ label=”Daily”]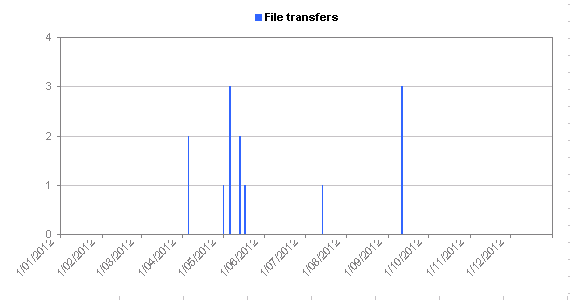 [/rn-tab]
[/rn-tab]
[rn-tab id=”2″ label=”Weekly”]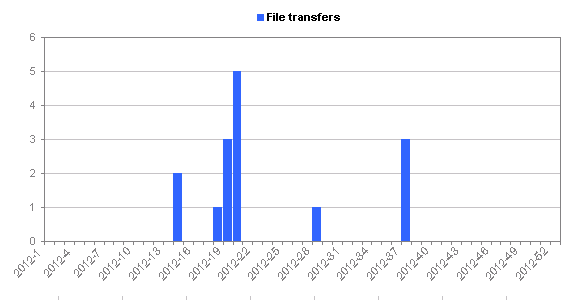 [/rn-tab]
[/rn-tab]
[rn-tab id=”3″ label=”Monthly”]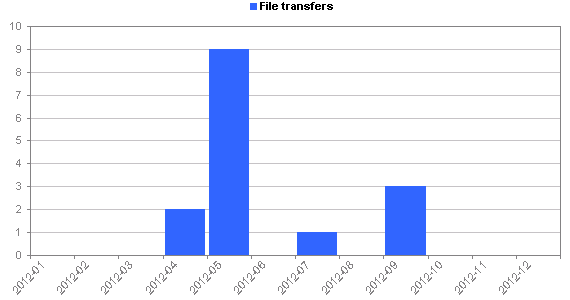 [/rn-tab]
[/rn-tab]
[/rn-tabs]
If you’re interested in the files people are downloading, the ones I’m seeing (with server names redacted to stop you from inadvertently clicking on the things):
- http://lost.in.████████.ro/haha.tgz
- http://lost.in.████████.ro/mata.tgz
- http://raydennn.████████.net/pico.tgz
- http://████████.se/wru
- http://download.microsoft.com/download/win2000platform/SP/SP3/NT5/EN-US/W2Ks
- http://download.microsoft.com/download/win2000platform/SP/SP3/NT5/EN-US/W2Ksp3.exe
- http://root-arhive.████████.am/scanner/gosh.jpg
- http://████████.ucoz.com/GeekzMech,.tgz
- http://www.████████.ro/redirecte_linux_v2.0.tar.gz
- http://████████.altervista.org/boti.tgz
- http://bucuresti.████████.net/R/D/N/udp.pl
- http://ddospower.████████.org/udp.pl
- http://inplm.████████.com/p.jpg
- http://copilash.████████/boti.tgz
- http://bucuresti.████████.net/R/D/N/ryo.tgz
- http://root-arhive.████████.ua/emech/emech-fast.jpg
- http://████████.ucoz.com/nethack.jp
- http://fitza.████████.su/sc/33180.tar
- http://a
- http://████████.djmixtv.net/puffu/gosh.tgz
which also includes a microsoft windows service pack in there, amusingly enough.
I would check out these .tar and .tgz archives to see what’s in there, but hey… only so many hours in the day.
And it’s always amusing to see the sorts of usernames/passwords that people attempt to jiggle the locks with, so:
Top 20 Login credentials
[rn-tabs id=”t7″ selected=”1″]
[rn-tab id=”1″ label=”Usernames”]
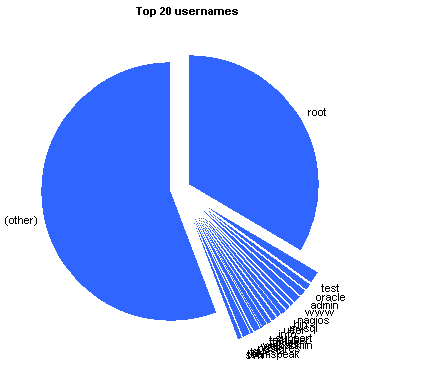
| root | 60513 | 33.680% |
| test | 2395 | 1.333% |
| oracle | 1484 | 0.826% |
| admin | 1441 | 0.802% |
| www | 1306 | 0.727% |
| nagios | 1160 | 0.646% |
| bin | 1153 | 0.642% |
| mysql | 1084 | 0.603% |
| user | 1062 | 0.591% |
| info | 970 | 0.540% |
| support | 967 | 0.538% |
| testuser | 759 | 0.422% |
| ftpuser | 744 | 0.414% |
| webadmin | 705 | 0.392% |
| web | 703 | 0.391% |
| postgres | 651 | 0.362% |
| guest | 591 | 0.329% |
| ts | 585 | 0.326% |
| teamspeak | 582 | 0.324% |
| svn | 551 | 0.307% |
| (other) | 100265 | 55.805% |
[/rn-tab]
[rn-tab id=”2″ label=”Passwords”]
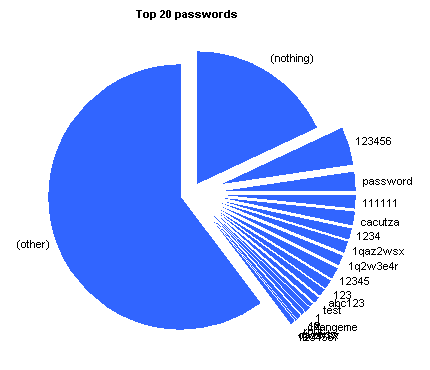
| (nothing) | 32625 | 18.158% |
| 123456 | 8217 | 4.573% |
| password | 4177 | 2.325% |
| 111111 | 3118 | 1.735% |
| cacutza | 2838 | 1.580% |
| 1234 | 2596 | 1.445% |
| 1qaz2wsx | 2517 | 1.401% |
| 1q2w3e4r | 2333 | 1.299% |
| 12345 | 2266 | 1.261% |
| 123 | 2160 | 1.202% |
| abc123 | 1583 | 0.881% |
| test | 1409 | 0.784% |
| 1 | 977 | 0.544% |
| a | 871 | 0.485% |
| 12 | 800 | 0.445% |
| changeme | 628 | 0.350% |
| root | 625 | 0.348% |
| qwerty | 525 | 0.292% |
| qazwsx | 515 | 0.287% |
| 1234567 | 471 | 0.262% |
| (other) | 108420 | 60.344% |
[/rn-tab]
[rn-tab id=”3″ label=”Username/passwords”]
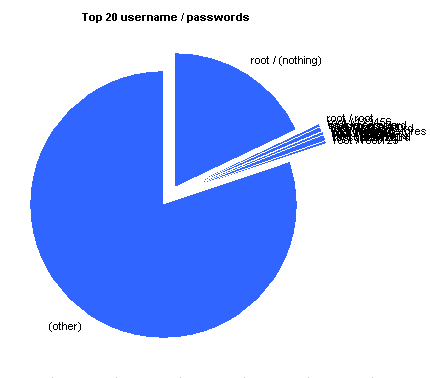
| root / (nothing) | 32586 | 18.137% |
| root / root | 557 | 0.310% |
| root / 123456 | 302 | 0.168% |
| root / password | 243 | 0.135% |
| oracle / oracle | 195 | 0.109% |
| test / test | 194 | 0.108% |
| root / P@ssw0rd | 163 | 0.091% |
| root / 111111 | 159 | 0.089% |
| root / qwerty | 150 | 0.084% |
| root / 1q2w3e | 132 | 0.074% |
| postgres / postgres | 129 | 0.072% |
| root / redhat | 127 | 0.071% |
| root / abc123 | 123 | 0.069% |
| root / 1234 | 119 | 0.066% |
| root / shit | 111 | 0.062% |
| root / passw0rd | 110 | 0.061% |
| mysql / mysql | 103 | 0.057% |
| test / test123 | 94 | 0.052% |
| root / abcd1234 | 93 | 0.052% |
| root / root123 | 85 | 0.047% |
| (other) | 143896 | 80.089% |
[/rn-tab]
[/rn-tabs]
The password selection here (second tab above the graph) also predominantly checks for the greatest passwords of all time
An interesting password in the top 10 was “cacutza” coming in at number five. It’s not as popular as “password”, but more popular than “12345”. I couldn’t find anything about it on the net, but according to a Romanian friend of mine, it’s not a word but is close to some urban slang that means prostitute, little shit or a poisoning plant. You learn something new every day 🙂
Top 20 IP addresses
[rn-tabs id=”t8″ selected=”1″]
[rn-tab id=”1″ label=”By connection”]
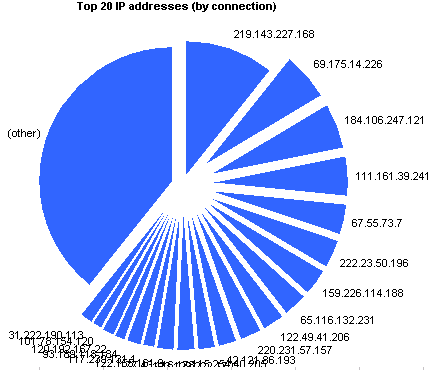
 |
219.143.227.168 | 15336 | 10.721% |
 |
69.175.14.226 | 8433 | 5.895% |
 |
184.106.247.121 | 7812 | 5.461% |
 |
111.161.39.241 | 6486 | 4.534% |
 |
67.55.73.7 | 5153 | 3.602% |
 |
222.23.50.196 | 4912 | 3.434% |
 |
159.226.114.188 | 4283 | 2.994% |
 |
65.116.132.231 | 4177 | 2.920% |
 |
122.49.41.206 | 3602 | 2.518% |
 |
220.231.57.157 | 3465 | 2.422% |
 |
42.121.86.193 | 3144 | 2.198% |
 |
115.254.40.205 | 2863 | 2.002% |
 |
123.129.222.170 | 2674 | 1.869% |
 |
177.43.116.178 | 2572 | 1.798% |
 |
122.155.161.9 | 2271 | 1.588% |
 |
117.239.131.1 | 2161 | 1.511% |
 |
93.189.118.184 | 1861 | 1.301% |
 |
120.192.167.22 | 1769 | 1.237% |
 |
101.78.154.120 | 1731 | 1.210% |
 |
31.222.190.113 | 1731 | 1.210% |
 |
(other) | 56603 | 39.572% |
[/rn-tab]
[rn-tab id=”2″ label=”by login attempt”]
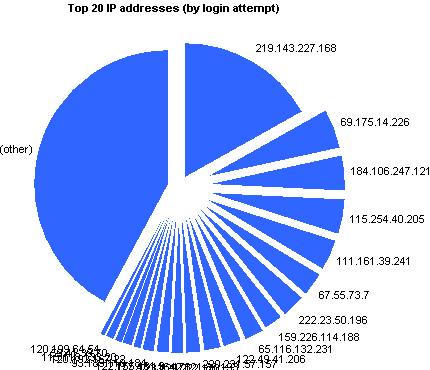
 |
219.143.227.168 | 30421 | 16.931% |
 |
69.175.14.226 | 8392 | 4.671% |
 |
184.106.247.121 | 7770 | 4.325% |
 |
115.254.40.205 | 7426 | 4.133% |
 |
111.161.39.241 | 6254 | 3.481% |
 |
67.55.73.7 | 5120 | 2.850% |
 |
222.23.50.196 | 4803 | 2.673% |
 |
159.226.114.188 | 4263 | 2.373% |
 |
65.116.132.231 | 4143 | 2.306% |
 |
122.49.41.206 | 3582 | 1.994% |
 |
220.231.57.157 | 3447 | 1.919% |
 |
42.121.86.193 | 3125 | 1.739% |
 |
123.129.222.170 | 2651 | 1.475% |
 |
177.43.116.178 | 2555 | 1.422% |
 |
122.155.161.9 | 2253 | 1.254% |
 |
93.189.118.184 | 1844 | 1.026% |
 |
120.192.167.22 | 1755 | 0.977% |
 |
115.118.133.20 | 1432 | 0.797% |
 |
59.41.39.70 | 1401 | 0.780% |
 |
120.199.64.54 | 1331 | 0.741% |
 |
(other) | 75703 | 42.134% |
[/rn-tab]
[rn-tab id=”3″ label=”by login”]
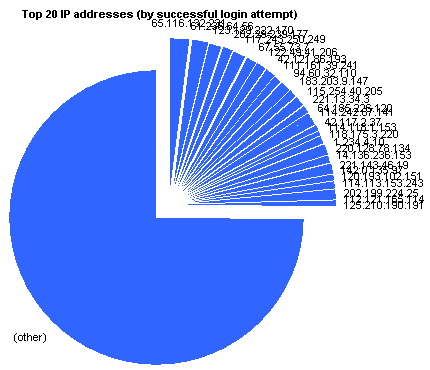
 |
65.116.132.231 | 107 | 2.299% |
 |
61.236.64.56 | 73 | 1.568% |
 |
123.129.222.170 | 65 | 1.396% |
 |
202.29.239.177 | 58 | 1.246% |
 |
117.243.250.249 | 55 | 1.182% |
 |
67.55.73.7 | 55 | 1.182% |
 |
122.49.41.206 | 53 | 1.139% |
 |
42.121.86.193 | 50 | 1.074% |
 |
111.161.39.241 | 45 | 0.967% |
 |
94.60.32.110 | 45 | 0.967% |
 |
183.203.9.147 | 44 | 0.945% |
 |
115.254.40.205 | 43 | 0.924% |
 |
221.13.34.3 | 41 | 0.881% |
 |
64.185.226.120 | 33 | 0.709% |
 |
114.242.87.141 | 31 | 0.666% |
 |
42.117.2.37 | 31 | 0.666% |
 |
114.118.1.153 | 30 | 0.645% |
 |
118.175.3.220 | 30 | 0.645% |
 |
1.234.4.10 | 30 | 0.645% |
 |
220.128.78.134 | 29 | 0.623% |
 |
14.136.236.153 | 29 | 0.623% |
 |
221.143.46.19 | 29 | 0.623% |
 |
142.0.135.97 | 29 | 0.623% |
 |
120.193.102.151 | 29 | 0.623% |
 |
114.113.153.243 | 29 | 0.623% |
 |
202.199.224.25 | 29 | 0.623% |
 |
112.121.165.114 | 29 | 0.623% |
 |
125.210.190.191 | 29 | 0.623% |
 |
(other) | 3471 | 74.629% |
[/rn-tab]
[rn-tab id=”4″ label=”by command (1)”]
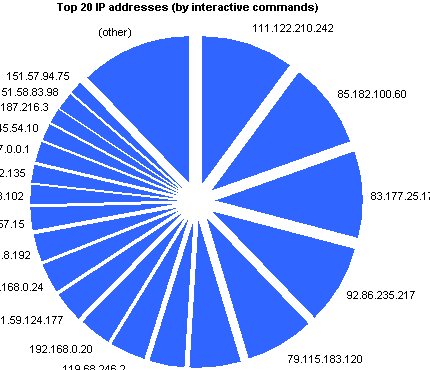
 |
111.122.210.242 | 41 | 10.406% |
 |
85.182.100.60 | 37 | 9.391% |
 |
83.177.25.176 | 37 | 9.391% |
 |
92.86.235.217 | 34 | 8.629% |
 |
79.115.183.120 | 29 | 7.360% |
 |
58.106.68.180 | 22 | 5.584% |
 |
151.81.79.80 | 16 | 4.061% |
 |
119.68.246.2 | 15 | 3.807% |
 |
192.168.0.20 | 14 | 3.553% |
 |
151.59.124.177 | 13 | 3.300% |
 |
192.168.0.24 | 13 | 3.300% |
 |
78.157.8.192 | 13 | 3.300% |
 |
62.36.57.15 | 9 | 2.284% |
 |
79.126.248.102 | 9 | 2.284% |
 |
86.35.192.135 | 8 | 2.031% |
 |
127.0.0.1 | 8 | 2.031% |
 |
216.45.54.10 | 8 | 2.031% |
 |
89.187.216.3 | 7 | 1.777% |
 |
151.58.83.98 | 7 | 1.777% |
 |
151.57.94.75 | 6 | 1.523% |
 |
(other) | 48 | 12.183% |
[/rn-tab]
[rn-tab id=”5″ label=”by command (2)”]
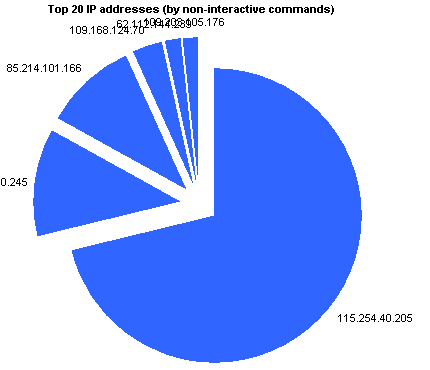
 |
115.254.40.205 | 42 | 71.186% |
 |
84.253.40.245 | 7 | 11.864% |
 |
85.214.101.166 | 6 | 10.170% |
 |
109.168.124.70 | 2 | 3.390% |
 |
62.112.144.239 | 1 | 1.695% |
 |
109.203.105.176 | 1 | 1.695% |
 |
(other) | 0 | 0.000% |
[/rn-tab]
[/rn-tabs]
I should probably point out that it’s relatively simple to proxy a login request through another machine, so it’s highly likely that the countries above aren’t a real indication of the source of the attacker. So remember to take that into account before you go and declare war on them.
Still, it makes the charts look pretty.
Location
[rn-tabs id=”t9″ selected=”2″]
[rn-tab id=”1″ label=”Cities (by connection)”]
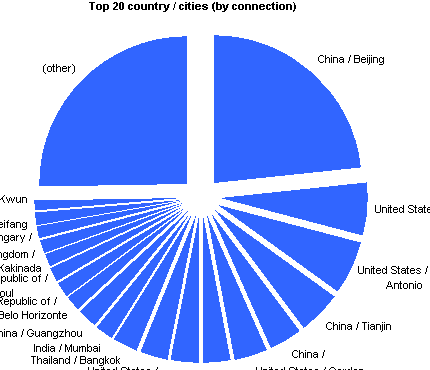
 |
China / Beijing | 33331 | 23.301% |
 |
United States / Chicago | 8565 | 5.988% |
 |
United States / San Antonio | 8211 | 5.740% |
 |
China / Tianjin | 6696 | 4.681% |
 |
China / | 5360 | 3.747% |
 |
United States / Garden City | 5153 | 3.602% |
 |
China / Jinan | 4345 | 3.038% |
 |
China / Hangzhou | 4314 | 3.016% |
 |
United States / Watertown | 4177 | 2.920% |
 |
Thailand / Bangkok | 4145 | 2.898% |
 |
India / Mumbai | 2908 | 2.033% |
 |
China / Guangzhou | 2802 | 1.959% |
 |
Brazil / Belo Horizonte | 2572 | 1.798% |
 |
Korea, Republic of / | 2478 | 1.732% |
 |
Korea, Republic of / Seoul | 2179 | 1.523% |
 |
India / Kakinada | 2161 | 1.511% |
 |
United Kingdom / | 2077 | 1.452% |
 |
Hungary / | 1903 | 1.330% |
 |
China / Weifang | 1769 | 1.237% |
 |
Hong Kong / Kwun Tong | 1731 | 1.210% |
 |
(other) | 36163 | 25.282% |
[/rn-tab]
[rn-tab id=”2″ label=”Countries (by connection)”]
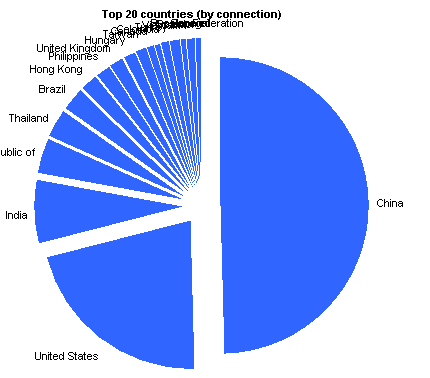
 |
China | 67812 | 47.407% |
 |
United States | 29562 | 20.667% |
 |
India | 9363 | 6.546% |
 |
Korea, Republic of | 5183 | 3.623% |
 |
Thailand | 4448 | 3.110% |
 |
Brazil | 3373 | 2.358% |
 |
Hong Kong | 2487 | 1.739% |
 |
Philippines | 2329 | 1.628% |
 |
United Kingdom | 2086 | 1.458% |
 |
Hungary | 1903 | 1.330% |
 |
Taiwan | 1274 | 0.891% |
 |
Canada | 1157 | 0.809% |
 |
Colombia | 1051 | 0.735% |
 |
Turkey | 920 | 0.643% |
 |
Vietnam | 797 | 0.557% |
 |
Spain | 764 | 0.534% |
 |
Ecuador | 731 | 0.511% |
 |
Japan | 682 | 0.477% |
 |
Senegal | 665 | 0.465% |
 |
Russian Federation | 625 | 0.437% |
[/rn-tab]
[/rn-tabs]
If I had even a shred of business nouse I’d throw that all into a webapp or bundle it into a programmable network appliance and get people to pay me, oh, $200 a pop for it. Leave a message in the comment sections below if you’re interested, incidentally.
Not that you can actually do that much with the information, but I guess it’s always nice to know what people are trying to do with random IP addresses out on the internet.
Especially if it’s your random IP addresses out on the internet.
Update 30/1/2013: Added the bit about cacutza in the password section.
Update 6/5/2013: If you find this interesting, you might also want to look at another kippo analysis at http://blog.macuyiko.com/2011/03/running-ssh-honeypot-with-kippo-lets.html .
Update 17/12/2023: So apparently this is now called cowrie, not kippo. Also noticed that someone else has produced some software to produce the same kinds of charts that I’ve got above. At some stage I’ll rejig all this for the cowrie server I kicked off a month or two ago.




Really interesting. You should take a look in those files! I’m curious. haha.tgz… gosh.jpg … they are downloading to your honeypot then down to thier own servers from there?
Yeah should do 🙂
As far as I can see it’s just to the honeypot… the honeypot allows the download to take place, but doesn’t let them unzip, view or run the downloads from there.
I might try to find some interesting sessions and transcribe the complete list of commands they enter up on the blog…
So, I just need to install, config Kippo and be connected to the net, using a static-manual public-IP, and there will be poeple willing to log-in to my faux-server?
Interesting…
Yeah, pretty much, I don’t think you even need a static IP, since I imagine there are people (and/or machines operating within the american homeland security bunkers) that are port-scanning the entire IP address space, but it would help as far as getting consistent data out of the thing.
I haven’t looked at the logs in a while… I guess I should probably write a script to keep these graphs up-to-date. It’d be interesting to see if I get higher or lower number of connection attempts to port 22 than to port 80.